FAIR Institute Expert Panel
Expert Panel and Q&A on quantitative risk analysis with FAIR.
Read MoreExpert Panel and Q&A on quantitative risk analysis with FAIR.
Read MoreMany companies are considering blockchain technologies to make transactions faster, more secure and cost effective. If you are performing risk analysis on these emerging technologies, you ask be asking yourself: how do I even start to analyze risk when there are so many unknowns? A successful analysis requires a paradigm shift in thinking into two areas: casting aside the defense-in-depth metaphor to describe security controls; and, how we assess and analyze risk of new and emerging technologies that have a high degree of uncertainty.
Read MoreFrom April 15–20 2018, the city of San Francisco hosts several simultaneous security conferences. The sub-field of quant, data driven cyber / information security / technology risk and metrics is very small, so I’ve started to compile a list of talks and events that week. To make it on this list, the talk should be about the sub-field described above OR presented by/hosted by someone who is active in that sub-field.
Read MoreThe term “Black Swan event” has been part of the risk management lexicon since its coinage in 2007 by Nassim Taleb in his eponymous book titled The Black Swan: The Impact of the Highly Improbable. Taleb uses the metaphor of the black swan to describe extreme outlier events that come as a surprise to the observer, and in hindsight, the observer rationalizes that they should have predicted it.
Read MoreJack Freund, of Measuring and Managing Information Risk fame, edited and released a new book titled Fintech: Growth and Deregulation. I’m happy to announce that I wrote a chapter titled “Cyber-risk Quantification of Financial Technology.”
Read MoreProbability estimates are the cornerstone of any good risk assessment in which data is sparse or expensive to come by, and are often thought of as one of the best ways to supplement existing information with subject matter expertise. Many risk analysts, however, can run into issues when trying to integrate the opinions of many subject matter experts into a risk management program.
Read MoreMy New Year’s Day ritual has been the same for nearly 10 years now: a late breakfast, a cup of strong coffee and a scan of security blogs and news for two things that always make me chuckle: cyber predictions for the new year, and a retrospective that declares the past year the “Year of the Data Breach.” Kelly Shortridge perfectly parodied the former and I actually thought we might go a year without the latter, until I found this headline on Bloomberg news in which 2017 is named the Year of the Data Breach.
Read MoreWould you be surprised to find that “nearly 40% of ransomware victims pay attackers,” according to a recent article published by DarkReading? I sure was. The number of victims that pay ransomware and the amount paid has been an elusive figure for years now. To date, law enforcement has not collected and published ransomware crime statistics like they have for other forms of criminal activity.
Read MoreSelection bias is what makes these surveys virtually worthless. I previously wrote about the problems of surveys in information security vendor reports and I want to dig in deeper on a topic from the last post: properly selecting a representative sample from the general population being surveyed. This matters so much. This is perhaps the most important step when conducting a statistically sound survey.
Read More“One typo” didn’t bring down Amazon’s S3; it’s a cascade of fail that goes up the chain of management
Read MoreThe information security vendor space is flooded with research: annual reports, white papers, marketing publications — the list goes on and on. This research is subsequently handed to marketing folks (and engineers who are really marketers) where they fan out to security conferences across the world, standing in booths quoting statistics and attending pay-to-play speaking slots, convincing executives to buy their security products.
Read MoreRansomware infections are nasty and potentially devastating events that can cripple large companies and home computers alike. Ransomware comes in many varieties and works in different ways, but the basic scenario is the same: cybercriminals infect your computer with malicious software that blocks access to your system or important files until you pay the ransom. You have a finite amount of days to pay if you ever want to see your files again.
Read MoreWhat do the San Francisco Giants, Cryptolocker and nuclear war all have in common? They all involve conflicts in which incentives, payouts and winning strategies can be analyzed with game theory. Game theory is a branch of mathematics that models conflict and cooperation between parties and is used in many real-world decision making scenarios, inside and outside the Information Security field. Game theory is particularly useful in analyzing the extortionist / victim dynamic present in ransomware infection scenarios.
Read More
FAIR Institute, SF Bay Chapter Meeting | San Jose, CA | November 16, 2016
A step-by-step walkthrough of performing a quantitative risk assessment based on FAIR on DDoS attacks.
Read MoreWord clouds are a great way to visualize text, especially on platforms like Twitter where a great amount of people can be talking about one subject. I recently spent the last 6 days at two San Francisco information security conferences: BSides San Francisco and RSA.
BSides this year was February 28–29 and RSA was February 29-March 4. There’s some overlap in attendees, but the talks and the feeling you get from being at the cons couldn’t be more different. BSides is community driven and the talks are mostly by security practitioners; RSA has a trade-show feel and most talks are conducted by people that work for security vendors.
I was curious about what words showed up most in tweets with the hashtags #BSidesSF and #RSAC and see how different or alike they were. I used the twitteR and wordcloud packages in R to generate these images.
Here’s #BsidesSF:

and here’s #RSAC:
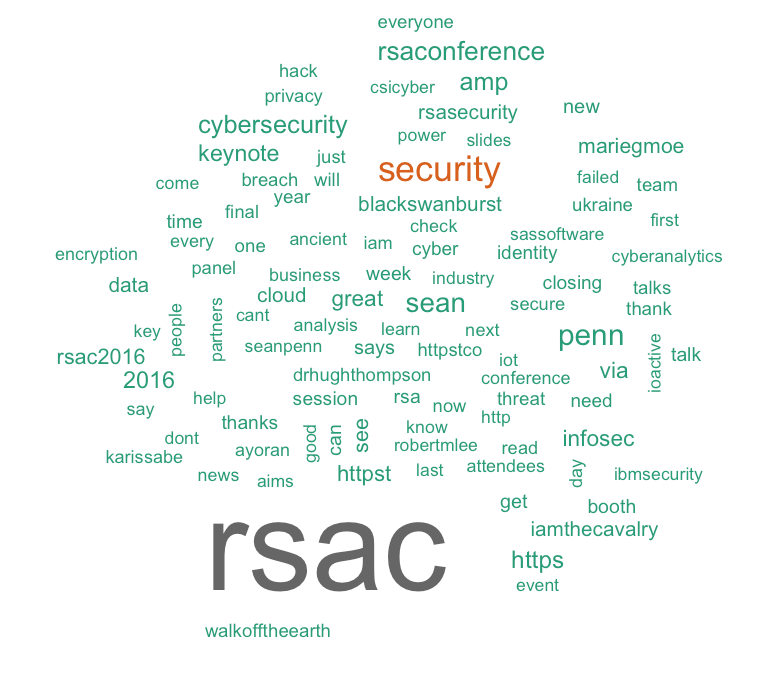
People were definitely tweeting about different things; BSides attendees generally had more positive language and tweeted about presenters. RSA attendees tweeted about keynote speakers (like Sean Penn) and contained a lot of retweets mentions. I am also not surprised the word “booth” was a top keyword in #RSAC, from vendors tweeting out “Come to our booth and get a free pen!”
It was interesting to see the similarities and differences. Let me know what you think.
Ransom is more than just the stuff of Hollywood thrillers. Action packed extortion schemes are as old as history itself, but today’s criminals are trading in information. Extortion rackets such as the Ashley Madison and Sony Pictures Entertainment hacks are well-known cases and many security professionals have experienced ransom attempts of their own, ranging from CryptoWall and CryptoLocker malware to DDoS attacks that promise to continue until the attackers are paid.
Read MoreThe DDoS extortion criminal group, DD4BC, has been hunted ever since the group’s formation in July 2014 by their victims and law enforcement.
One of their first victims, Bitalo Bitcoin Exchange, issued a 100 bitcoin bounty in November 2014 for information on the full and proven identity of the perpetrators. Additionally, an international cooperation of law enforcement has been tracking the group for over a year and a half. DD4BC’s luck finally ran out. On Jan. 12, Europol announced that one person has been arrested and another detained as part of Operation Pleiades, a cooperative investigation that included law enforcement agencies from Austria, Bosnia and Herzegovina, Germany, the UK and Europol.
Read MoreIs using ad blocking software stealing or is it a sound security practice?
On one hand, many websites and content creators make money from advertising. They certainly deserve to be compensated for their time and effort. On the other hand, advertising — at best — can be annoying, and at worst, can serve up malware, suck up bandwidth and redirect confused users to websites without their knowledge.
Read MoreIn May, Lastpass announced an intrusion on its network that led to a data breach of user account information. LastPass is a cloud-based password manager; users load the LastPass extension into their web browsers and all the pesky password management tasks are taken care of. The user is given one-click access to fill in the username and password on known sites and the option to generate a long password and save credentials on new sites.
Read More